#flexibility
Strengthen the autonomy and engagement of your participants
With Teasio, each participant has access to a clear and structured space where they can find all their steps, documents, and materials at any time.
This guiding thread allows support to continue between sessions, keeps a record of progress, and strengthens the understanding and ownership of the content.

#independence
Make your coachees more independent.
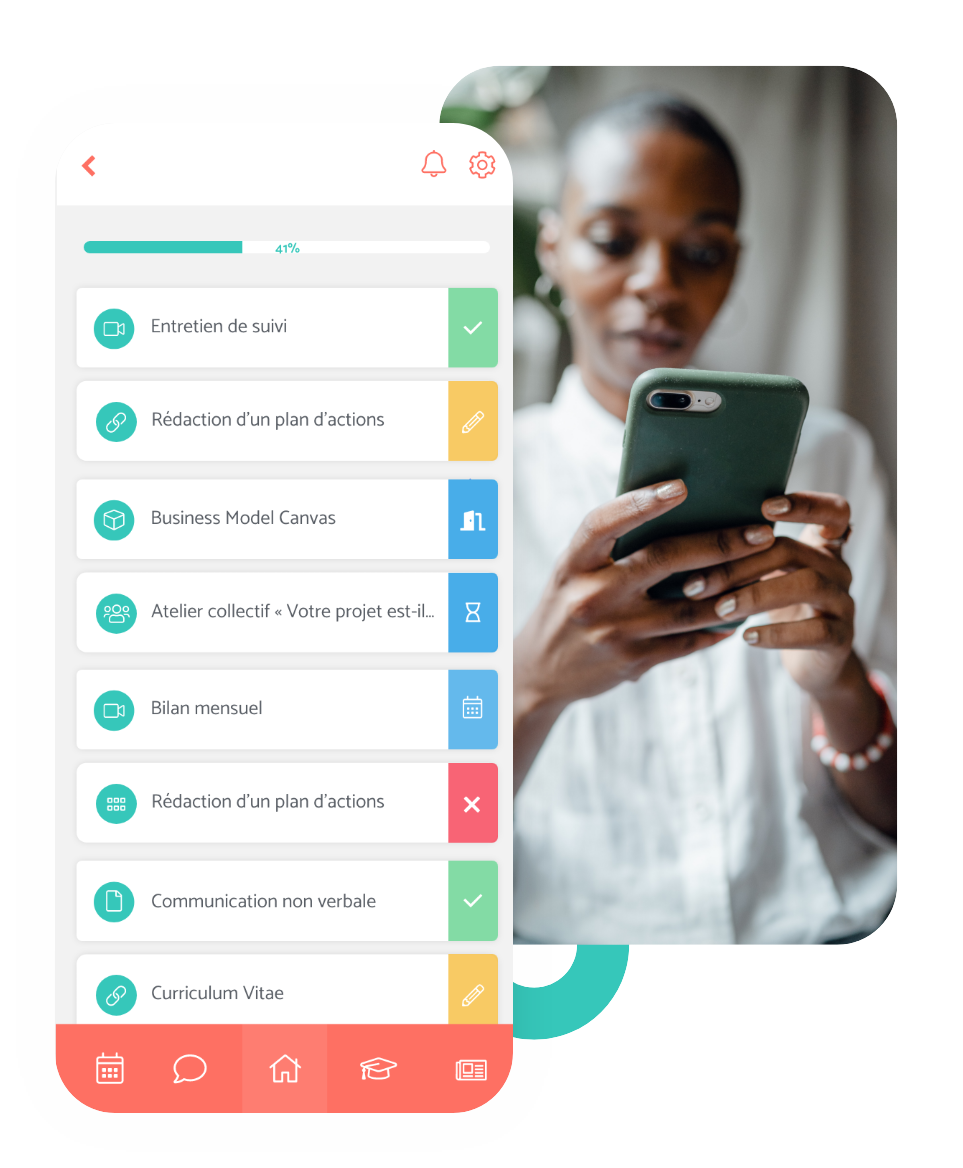
The Teasio programme leaves a record of your coaching sessions which represents a real added value compared to traditional coaching sessions. Coachees can refer back to the various steps of their programme and have access to their documents as often as they wish.
The Teasio programme leaves a record of your coaching sessions which represents a real added value compared to traditional coaching sessions. Coachees can refer back to the various steps of their programme and have access to their documents as often as they wish.

Value your clients' skills.
At the end of a program, it is possible to award a micro-certificate, attesting to the progress made and the skills applied throughout the journey. A simple way to acknowledge efforts, formalize learning, and enhance the perceived value of your support.

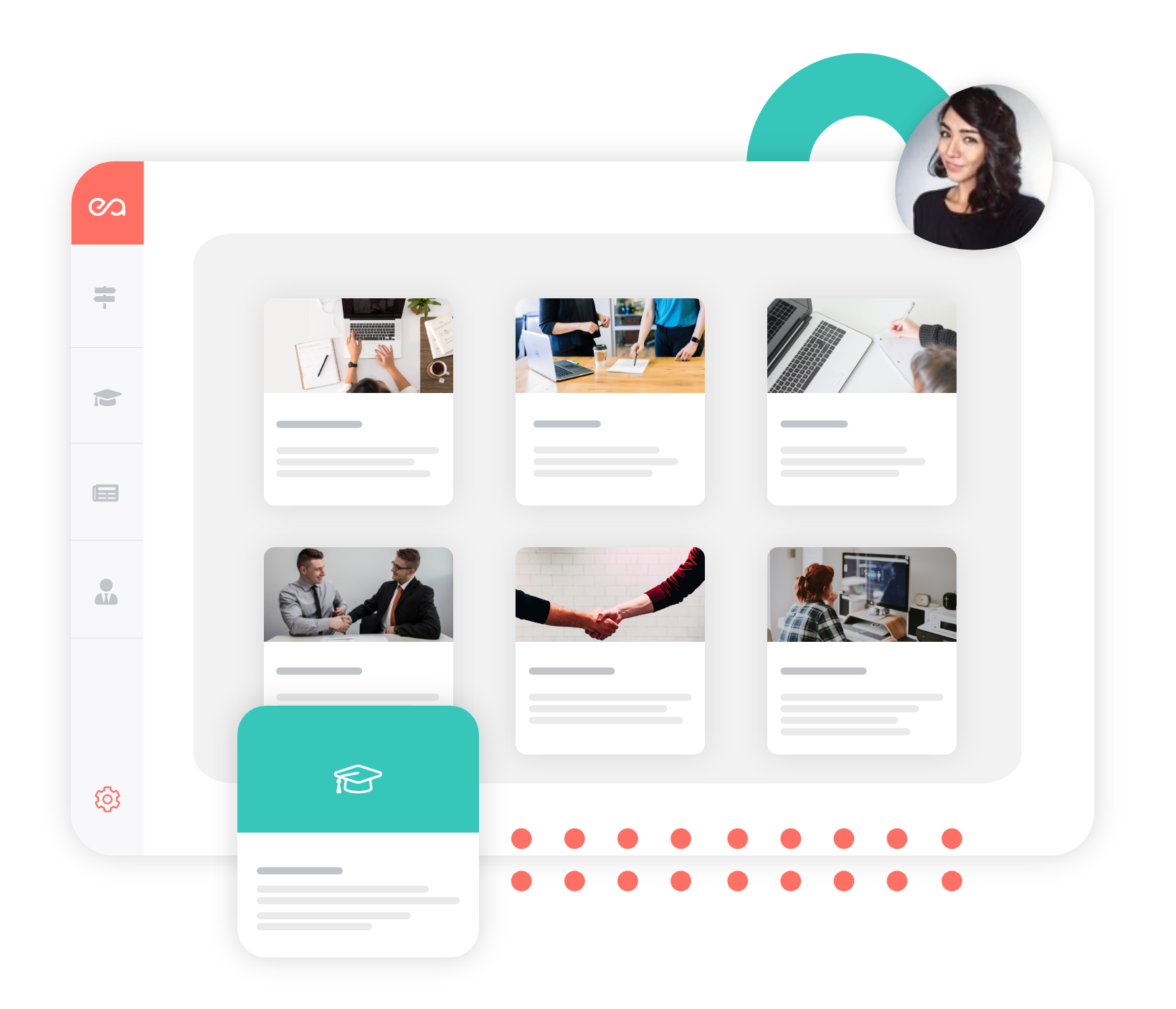
Engage your community
The skills center, accessible to participants alongside their program, allows you to share cross-cutting content, organize group sessions (webinars, workshops…), and create a flexible, sustainable learning dynamic. A simple tool to foster connections, promote autonomy, and keep your community active every day.
That’s not all
Teasio provides you with
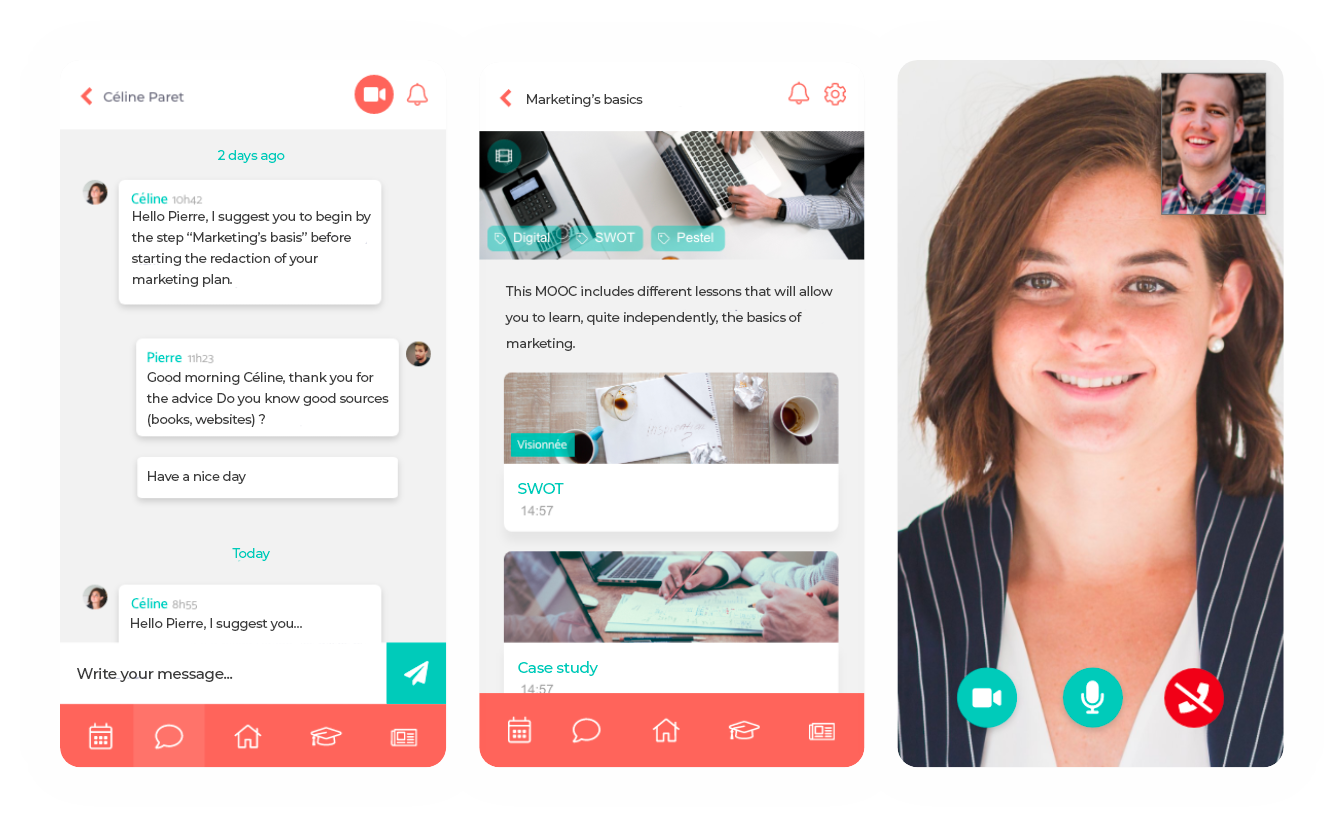
Mobility
In your customer’s pocket
Teasio’s mobile app is one of the most comprehensive on the market. Packed with features and highly intuitive, this app could constitute the distinctive element of your organisation.


Connectivity
Connected for greater simplicity
Today, a web platform must be interconnectable. Teasio can be synchronised with apps you already use. We’ve created a secure API allowing your developers to connect to Teasio, collect the data they need easily and connect to your internal applications. We’ve also developed connectors like Zapier or Slack in order to be able to connect Teasio to a multitude of apps. At Teasio, we’re intent on making your life easier.

Security
Your security is our priority
Teasio includes a number of safeties which currently allow us to satisfy even the most demanding customers.
Protecting your data is essential
Within the GDPR framework, we offer a series of tools allowing you to have a guarantee of your users’ consent as well as ensuring the protection of their data.
Strong password
Intrusion detection
Encryption of sensitive data
Automatic
logout
HTTPS protocol
Access control management
Data segregation

etc.